
In our digital age, Android apps play a central role in users’ lives, handling a wealth of sensitive information such as personal details, payment credentials, and authentication tokens. With the growing risk of data breaches, developers must prioritize security to safeguard user data and maintain trust. This blog post explores why data security is essential in Android development and introduces several core tools, including EncryptedSharedPreferences, the Android Keystore System, and network security configuration, to help secure data and prevent unauthorized access.
Why Data Security Matters in Android Development
Data security is fundamental to building user trust. When users install an app, they expect that their personal information will be handled with care. Any breach of this trust can damage an app’s reputation, result in costly legal consequences, and negatively impact business goals. With Android’s diverse device ecosystem and variations in OS versions, creating a secure environment for user data is crucial for developers. Not only does it ensure regulatory compliance (e.g., GDPR, CCPA), but it also promotes a safer digital experience for users.
Essential Tools for Securing Data in Android Apps
The Android platform offers several powerful tools that help developers secure data and manage sensitive information. Here, we’ll look at three essential tools that can enhance data security in Android applications:
1. EncryptedSharedPreferences
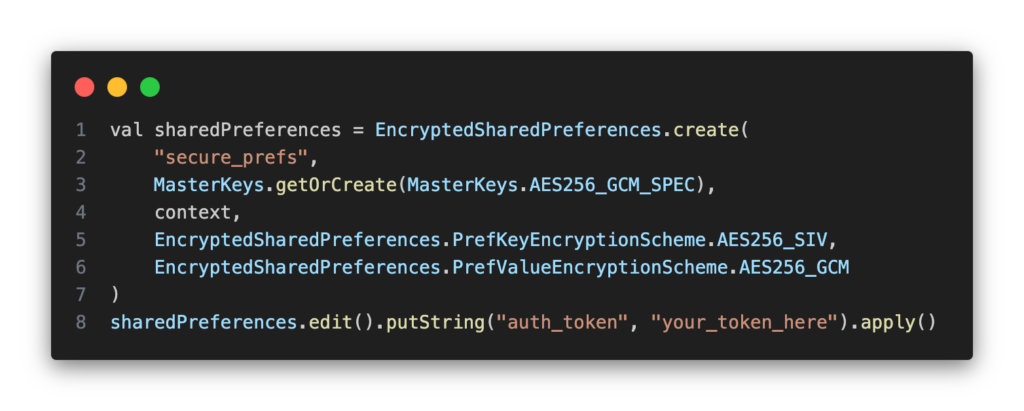
SharedPreferences is a popular storage solution for Android apps when it comes to saving small amounts of key-value data. However, by default, SharedPreferences doesn’t provide encryption, which could expose sensitive information to unauthorized access. EncryptedSharedPreferences offers a secure alternative.
What It Does: EncryptedSharedPreferences enables developers to securely store key-value data by encrypting both keys and values.
How It Works: It uses AES-256-bit encryption, securing data at rest and making it accessible only to the app that created it.
Use Cases: Use EncryptedSharedPreferences to store sensitive data like API tokens, user credentials, or session information. It’s also ideal for storing information that doesn’t need to be shared across devices.
2. Android Keystore System
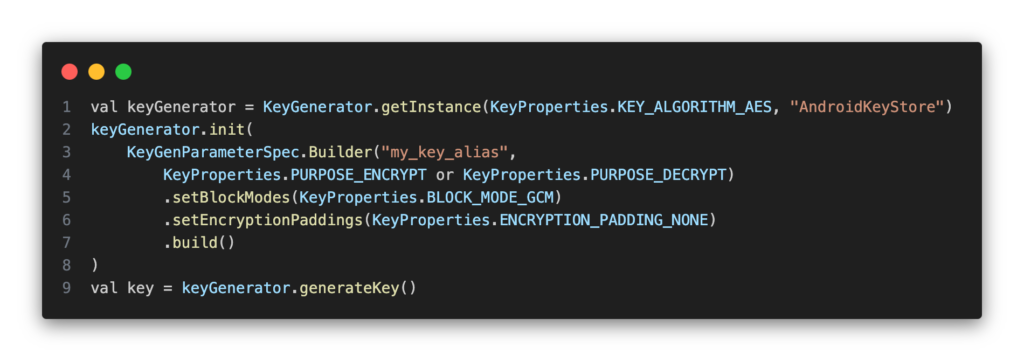
The Android Keystore System provides a secure environment to store cryptographic keys and perform cryptographic operations without exposing the actual keys to the application.
What It Does: The Keystore system allows apps to securely generate and store cryptographic keys. It prevents these keys from being exported or tampered with, enhancing the security of sensitive operations.
How It Works: Keys generated and stored within the Keystore are kept secure and can only be used within the Keystore. This isolation helps protect the keys from malicious attacks and unauthorized access.
Use Cases: The Keystore is ideal for securing sensitive data and keys that are required for authentication, encryption, or digital signing. For instance, you could use it to encrypt sensitive user data or manage access tokens for secure API communication.
3. Network Security Configuration
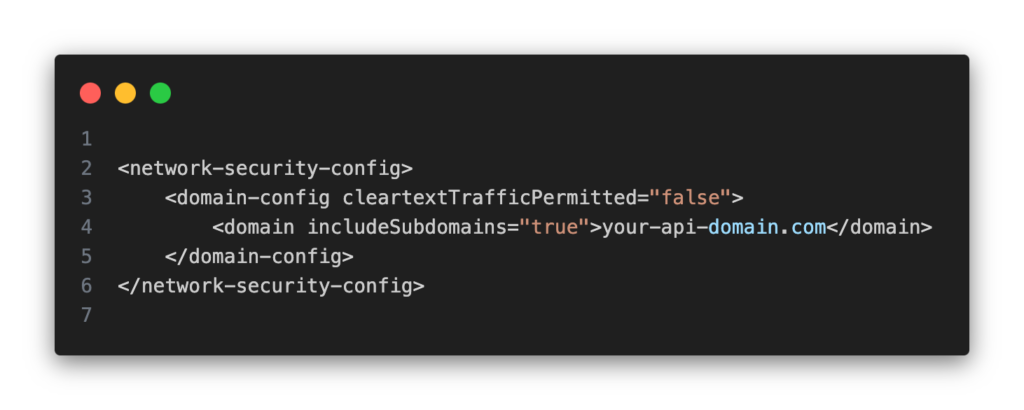
Network Security Configuration is a powerful Android feature that lets developers define security settings for their app’s network connections. This configuration provides an additional layer of security, especially when communicating with remote servers
What It Does: Network Security Configuration enforces HTTPS connections, specifies trusted Certificate Authorities (CAs), and blocks cleartext (unencrypted) traffic by default.
How It Works: Developers can define a network security XML file with rules that dictate how the app handles network requests, enhancing protection against attacks like “man-in-the-middle” that can compromise sensitive data in transit.
Use Cases: Network Security Configuration is crucial for securing API requests, especially those that send user information over the network. It helps ensure that communication between the app and server is encrypted and protected from interception.
Best Practices for Data Security in Android Apps
While using the above tools provides a foundation for data security, following certain best practices can further protect sensitive data:
1. Always Use HTTPS: Ensure all API requests are made over HTTPS to prevent data interception.
2. Store Minimal Data Locally: Only store data locally if it is absolutely necessary. For sensitive data, consider using secure cloud storage options.
3. Implement Proper Authentication and Authorization:Use OAuth, token-based authentication, or biometric authentication where possible.
4. Apply Regular Security Audits: Conduct code reviews, dependency checks, and regular security audits to identify and fix potential vulnerabilities.
Wrapping Up
Data security is a vital consideration in Android development, and Android provides developers with several tools to protect sensitive data from unauthorized access. By using EncryptedSharedPreferences for secure local storage, leveraging the Android Keystore System for key management, and setting up a secure network configuration, developers can create a safer environment for users’ data. With careful implementation and secure coding practices, Android developers can help foster trust and create applications that prioritize users’ privacy and data security.